2025.3 Releases
This documentation outlines all releases for Q3 2025.
Release 7.2
Build Number: 29 Release Date: 09/26/2025
Data Testing
Connectors
Support has been added for the following connectors and authentication types:
| Connector | Authentication Type |
|---|---|
| CockroachDB | Username & Password |
| Yugabyte | Username & Password |
| Apache HBase | Kerberos |
| Apache HBase | Username & Password |
| SAP ECC (RFC)* | Username & Password |
Note: Everything marked with * has been moved from Beta to GA.
Rule Versioning
We’ve added powerful versioning capabilities to help teams collaborate, track changes, and maintain full control:
- Enable or disable versioning per workspace (history always retained).
- Create, compare, comment, and tag versions of Rules & Workflows.
- Restore, lock, or branch off a new Rule from any version.
- Check In/Check Out flow with approvals ensures controlled publishing.
- Debug mode for safe test runs before publishing.
BI Report Testing
- Add support of Power BI XMLA connector.
Improvements
- Added support for TSQL in Recon and Validation rules with SQL Server connector.
- Added support for Cursor and PLSQL in Recon and Validation rules with Oracle connector.
- Create or update Workflows with Rules directly from the Rule Listing page.
- Import Checks: Bulk creation of checks via JSON or XLSX upload, with sample templates provided.
- Parameter Change Log: Easily track, review, and compare all updates made to parameters
- Unified search across Rules, Workflows, Parameters, and Instances — supports both ID-based and text-based queries (Name, Code, Description).
- Rule Emails now include a Parameters section showing key values, with the option to download the full list of parameters used during execution.
- Workflow Alerts now include an HTML summary attachment with workflow overview, execution results, run summary, and detailed activity information. (Attachments over 5MB are delivered as zipped files.)
- Job Scheduling: Jobs added to schedules can now include Rules in addition to Workflows.
- Client Credentials: Users can now generate and manage client IDs directly from Administration → Security, with the ability to create and revoke credentials.
- Token Management: Available under the Token Generation tab in the User Profile page for easier access and control.
Note: 10+ additional refinements and usability improvements for a faster, smoother, and more intuitive experience.
Bug Fixes
- Exception Reports now download successfully even when record counts exceed 1 million.
- Fixed Snowflake connections not redirecting to configured proxy servers.
- Resolved failures with Rules containing large XML data and ORDER BY, which previously returned exit code -53.
- Addressed Java Heap Space errors during execution on very large datasets.
- Corrected data mismatches in Exception Reports caused by extra line breaks.
Non-Functional Improvements
- Standardized pod user IDs for consistency and security.
- Optimized database performance for faster operations.
- Streamlined Helm charts with cleaner code and improved image management.
- Enhanced RabbitMQ performance, boosting speed and scalability across workflows and core services.
Vulnerability Fixes
Security has been further strengthened in this release with 235 vulnerabilities resolved across multiple services and base images. The fixes span a wide range of libraries and frameworks, including but not limited to: Reactor Netty / Spring Boot, BusyBox base images, Amazon Corretto / OpenJDK, libxml2, Media toolchain (FFmpeg / Chromium / OpenEXR),
| Severity | Resolved |
|---|---|
| High | 64 |
| Medium | 72 |
| Low | 99 |
These fixes further strengthen platform security and reduce potential risks
Release 7.1
Build Number: 28 Release Date: 07/17/2025
Data Testing
Connectors
We have added support for the following connectors and authentications to be used in rules.
| Connector | Authentication Type |
|---|---|
| Rest API | API Key, Basic, Bearer, OAuth & No Auth |
| SAP ECC* | Username & Password |
| Excel (Azure Blob Storage)* | Azure Service Principal |
| Flat File SQL (Azure Blob Storage)* | Azure Service Principal |
| Flat File Native (Azure Blob Storage)* | Azure Service Principal |
We have added crawling support for Oracle, Teradata, SAP ECC*, Snowflake, SQL Server, Redshift, Google BigQuery, Databricks*. This will provide users with faster responses when creating rules and generating SQL using LLMs.
Note: Everything marked with * is in beta.
API Testing
With the release of the API Connector, users can now test data from their GET and POST APIs in iceDQ. To support this, we have added two new types of Rule Templates, API Validation and API Recon. Both the templates always use an API Connector as the source.
 |
|---|
Export Import
Users can now export and import Rules and Workflows across data testing workspaces within the same instances or across instances of iceDQ. We have released the following APIs.
| Name | Method |
|---|---|
| Export Rules | POST /api/v1/exports/rules |
| Export Workflows | POST /api/v1/exports/workflows |
| Status of Export task | GET /api/v1/exports/<task-instance-id>/status |
| Logs of Export task | GET /api/v1/exports/<task-instance-id>/log |
| Download Exported File | GET /api/v1/exports/<task-instance-id>/download |
| Terminate Export task | POST /api/v1/exports/<task-instance-id>:terminate |
| Import Rules | POST /api/v1/imports/rules |
| Import Workflows | POST /api/v1/imports/workflows |
| Status of Import task | GET /api/v1/imports/<task-instance-id>/status |
| Logs of Import task | GET /api/v1/imports/<task-instance-id>/log |
| Terminate Import task | POST /api/v1/imports/<task-instance-id>:terminate |
BI Report Testing
Users can now connect and test their Qlik Cloud Dashboards and Reports from iceDQ.
Key Features
- Auth Type: Users can connect to Qlik Cloud using Qlik App OAuth.
- Flexible Filtering: Users can filter data using Bookmarks or Filter Pane.
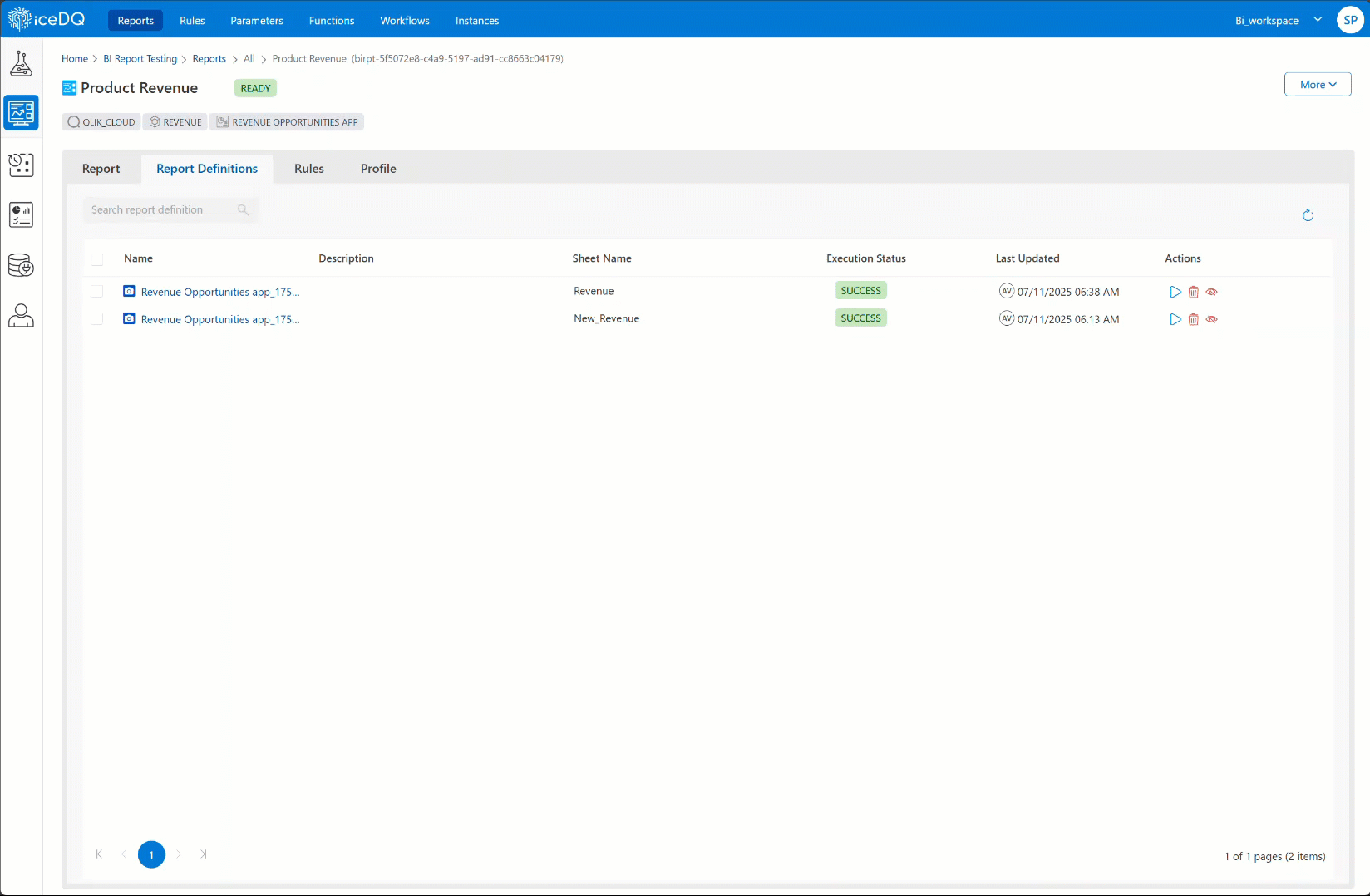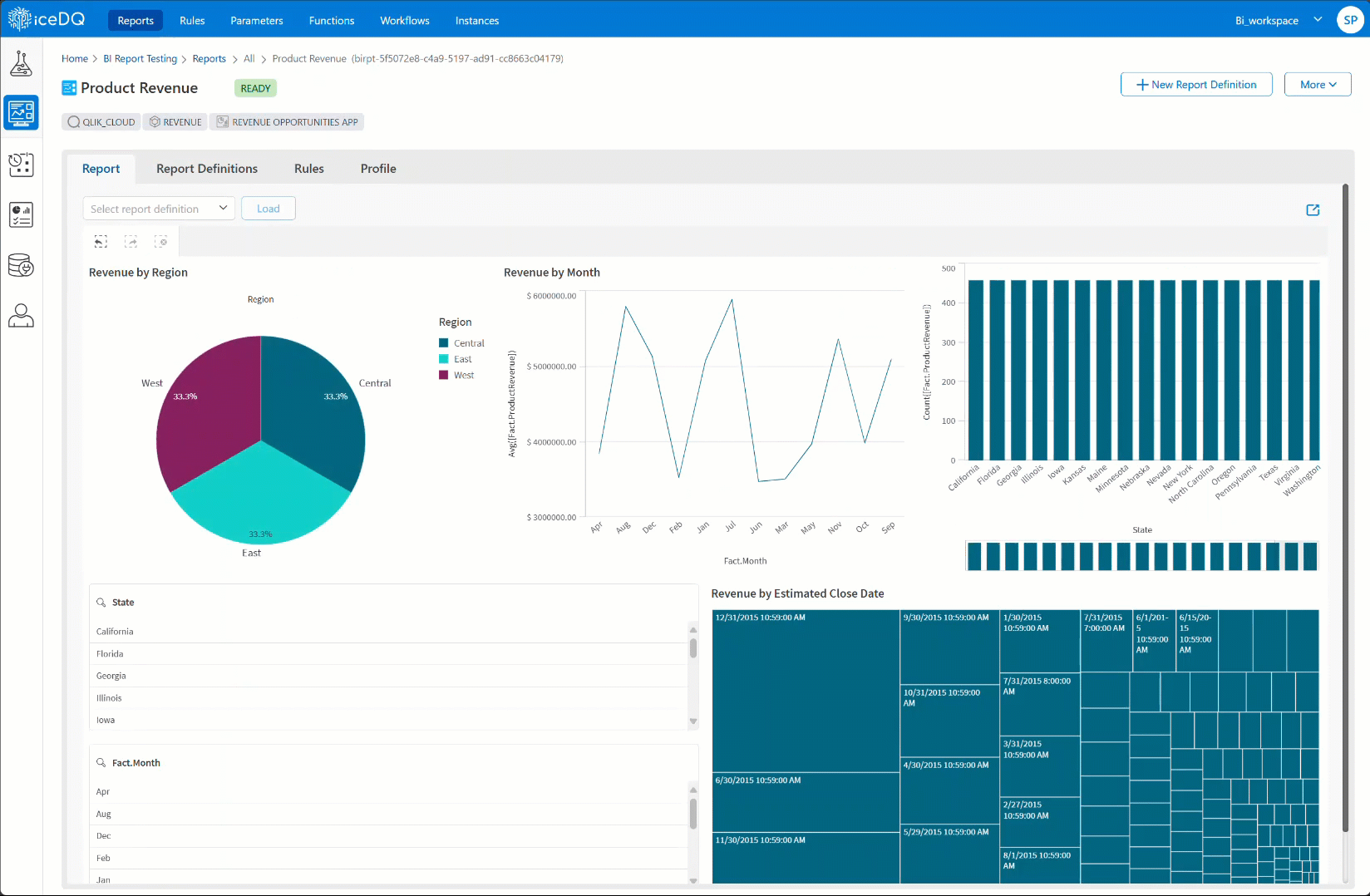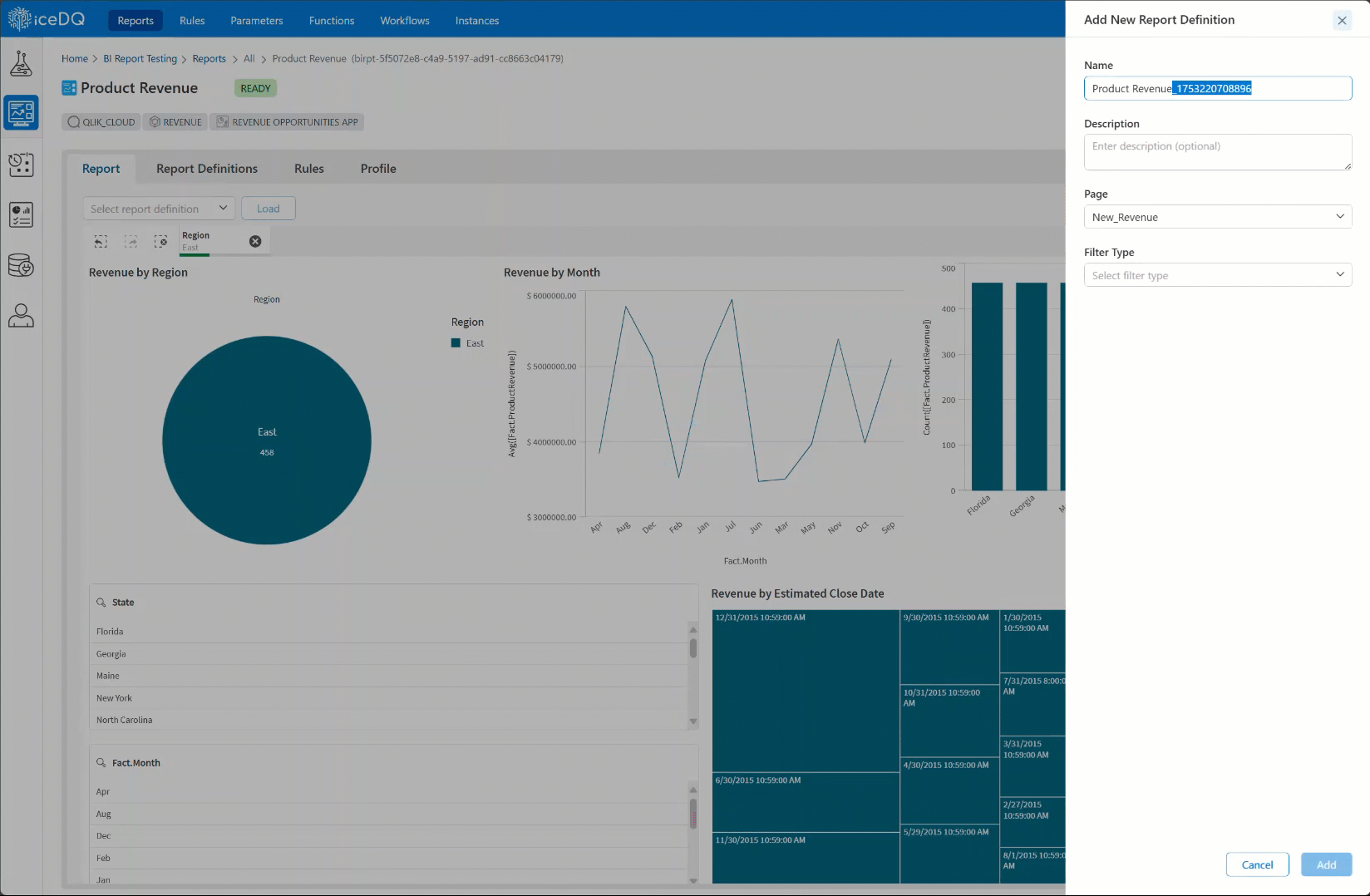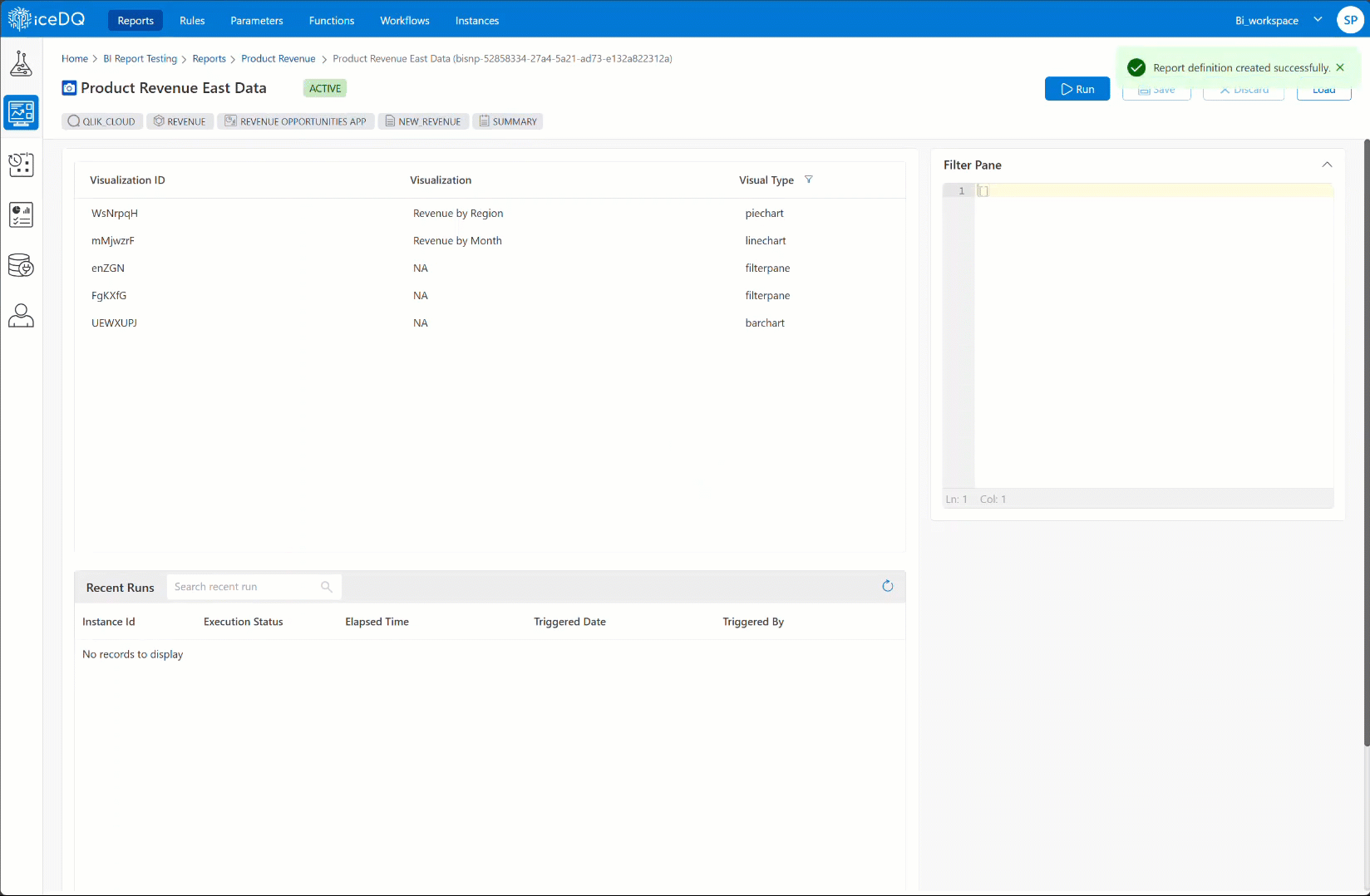 |
|---|
Improvements
- Users can now create checks in bulk by uploading an Excel file and a JSON schema file, enabling faster and more efficient setup of multiple checks.
- Added support for encrypted private keys in Snowflake Key Pair authentication.
- Added support for Programmatic Access Tokens in Snowflake Username and Password authentication.
- Made the Warehouse field mandatory when creating or updating Snowflake connections.
- Added support for .dat file extensions in Flat File (SQL) connectors during rule creation and file uploads.
- Enhanced the Oracle connector to display timestamp values in exception reports and preview data for
DATEdatatype columns using the useDateAsTimestamp property.
Bug Fixes
- Fixed an issue where the provided secret was not visible at the connection level.
- Fixed an issue with publishing Script Rules using External Libraries.
- Improved performance for Flat File (SQL) connection testing when the S3 bucket size is large.
- Added Account Name display after the workspace name in the workspace selection drop-down.
Note: Over 100+ other bugs have also been resolved in this release.
Vulnerability Fixes
- 168 vulnerabilities have been resolved across multiple components, resulting in improved application security.
- The fixes span a wide range of libraries and frameworks, including but not limited to: commons-beanutils, glibc, netty, OpenJDK, libxml2, fileupload, parquet, tomcat, zookeeper, keycloak, postgresql, and spring.
- 4 vulnerabilities remain open, while 60 newly discovered vulnerabilities have been identified.
| Severity | Resolved | Not Resolved |
|---|---|---|
| High | 53 | 2 |
| Medium | 57 | 2 |
| Low | 58 | 0 |
Known Issues
- Some connectors display certain data types inconsistently with and without preview when the Use Metadata Cache option is enabled.
- Crawl jobs fail to detect database, schema, or table names if filters are wrapped in double quotes, even when the filters are valid.
- No error message is shown when a rule's check name begins with a numeric character.
- Users with group-level access are unable to view dashboard access or workspace lists.